5 Online Safety Rules
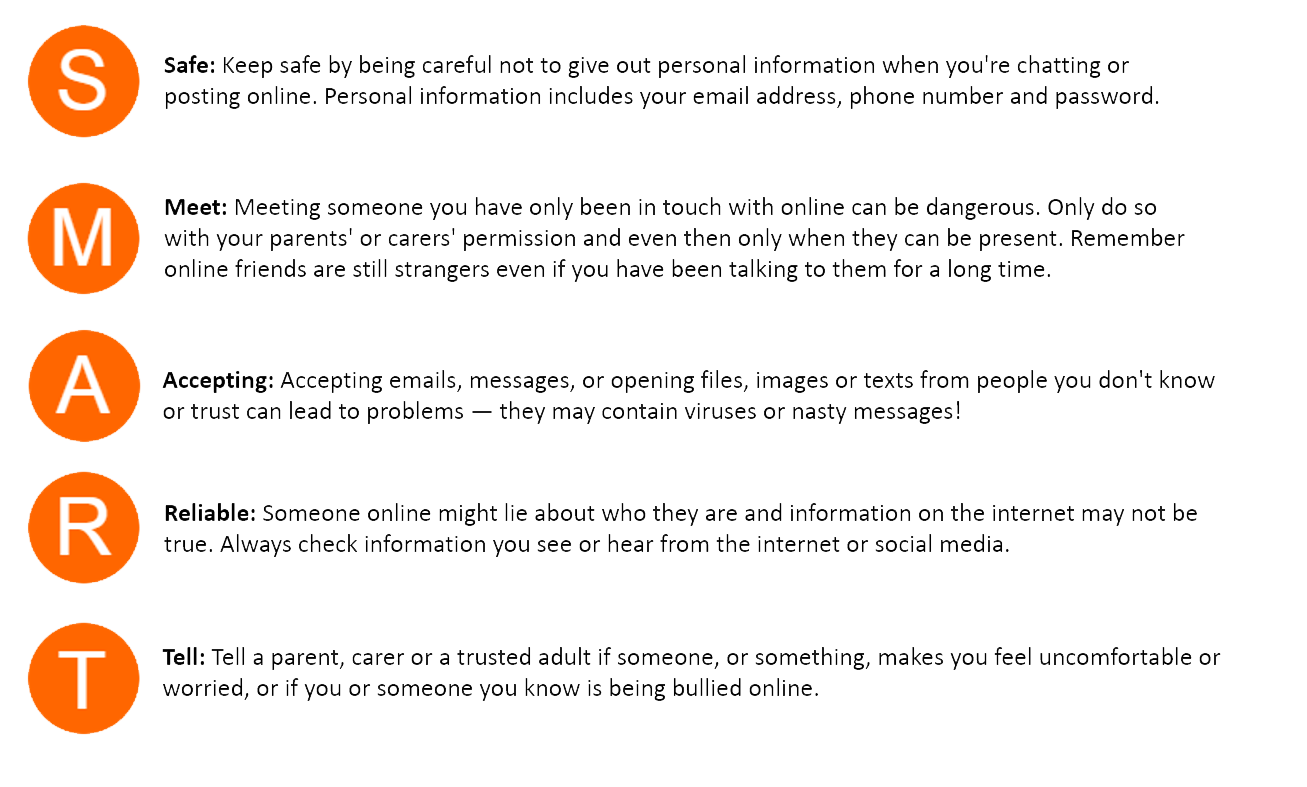
The five rules of E-Safety A.K.A S.M.A.R.T Safe-staying safe on the internet- have you got a good internet security program to stop viruses? Meeting- NEVER meet with someone that you have talked to on the internet unless they are friends you have known for a long time.

- Online safety guide 0-5 year olds. Online safety guide 6-10 year olds. Online safety guide 11-13 year olds. Online safety guide 14+ year olds. Moving to secondary school. Secondary school. Online pressures Secondary School. Digital resilience toolkit 6 – 10 year olds.
- A 19-year-old running for public office in New Hampshire found out about the importance of following Internet safety rules the hard way. As Seacoast Online reports, his opponents found images in his social media posts that were sexually suggestive and referenced past drug use. Just like that, his political career crashed and burned upon takeoff.
- I will always use good 'netiquette' and not be rude or mean online. Note: All Cyber Chips will expire annually. Each Scout will need to “recharge” the chip by going back to the NetSmartz Recharge area. This space will hold new information, news, and a place for the Scout to recommit to net safety and netiquette. Then, with the unit.
Avoiding the dark corners of the Internet
The Internet is a melting pot of information, social interaction, entertainment, and countless other resources that we rely on daily. It is literally limitless and constantly growing for both the better and worse. Are you following a few basic guidelines to make sure you don’t stumble into the dark side of the online world where the scammers, hackers, and infiltrators are waiting to take advantage of you? If not, here are 5 online safety rules to follow for good measure.
Important Rule #1
Always have anti-virus software that regularly scans your computer to detect and prevent viruses. This can also minimize damage if a virus actually invades your computer.
Important Rule#2
Don’t fall for scams. This includes but is not limited to: popups, ads that sound too good to be true, strangers offering awards or free gifts, job offers making a fortune working from home, congratulations you’re the millionth customer pitch, random surveys, forms that require credit cards, and many other vague advertisements.
Important Rule#3
Research a company before you give them any personal information. If you plan to buy something from their website, try and learn as much as you can about them before you make the purchase. If you have a gut feeling that this seems a little off kilter, then don’t do it!
5 Smart Rules To Online Safety
Important Rule#4
Don’t download files from untrusted websites. If you see an offer for a free. software download, it has the potential to infect your computer.
Important Rule #5
Stay away from suspicious websites at all. Suspicious characteristics include but are not limited to: abundant popups, shady side ads, and uncertain links. Stray away from these because one wrong click could send problems straight to your computer.
Cybercriminals are not only focusing on enterprises and SMBs but also targeting individual end-users like you.
Open Firefox Monitor, enter your email ID and see if it was the part of any data breach. You may be shocked to find your email ID featuring in multiple security breaches.
Phishing, vishing, pharming, ransomware, crypto-jacking – there are more versions of cybercrimes than you’d care to count.
The solution – understand and follow the five proven effective rules of cyber safety.
1- Take Passwords Seriously, Very Seriously
It’s unfair, though realistic, that a seemingly meaningless leaked string of characters could literally ruin your life. Your password is your first line of defense to protect your online identity.
Sadly, 86% of passwords are ‘terrible’. Using brute-force techniques, cybercriminals can try out millions of passwords within minutes. This means that if you’re using a password that’s in the mega list of half a billion compromised passwords, you are running a big risk.

The best practice – Never reuse a password across different websites. Build a ‘formula’ of setting up a password, which ensures that you use some combination of characters from the website name to build your password. This practice ensures you can confidently create a new password for each website, without the fear of having to remember them all.
Use a service such as Have I Been Pwned to find out whether your email ID has been compromised in a data security breach, which could have revealed your password.
2- Invest time, money, and effort in enhancing your awareness
You won’t combat what you don’t understand. The cybersecurity landscape is evolving and changing at a breakneck pace. Evaluate your stakes, understand the level of expertise you need, and be prepared to invest your resources accordingly.
If you’re a business owner or enterprise decision-maker, enroll yourself in personalized cybersecurity training, awareness, and readiness programs. If you’re a freelancer, student, web enthusiast, subscribe to newsletters from cybersecurity blogs to remain in the know-how of the latest threats.
3- Always use a VPN while browsing the web
Virtual Private Networks (VPNs) hide your web identity, thereby enabling you to browse the Internet while remaining protected from cybercriminals.
VPNs offer several other benefits:
- They ensure your information is encrypted, which saves you from the risks of data theft.
- VPNs let you unblock websites that may be restricted because of your geographic location, and bypass content filters.
- If you need an IP from a specific country, a VPN can help you with that. Take NordVPN for example, which lets you access content from any country, with its 5112+ servers located in 59 countries.
And you don’t even have to spend a lot. Use proven effective tips to save money while using Internet, and still remaining fully secure. Several VPN service providers offer you free trials, which means you can experiment with a lot of them, and only need to pay once you know you’ve found something suitable and affordable.
4- Don’t download anything from a website or content provider whom you don’t trust
There’s simply way too much at stake! Ransomware attacks are perpetrated via malware that runs on the victim computer terminal, because it’s cloaked under a seemingly harmless and safe program. Phishing attacks, which attempt to get the end-users to download malware on their computers, are on the rise.
- For computer programs, always download executable files from the software developer’s official page or a credible app store.
- For media, go for streaming services rather than shady online databases of downloadable files.
- Always keep your anti-malware software up to date and running.
5- Be careful what you post
Cybersecurity related laws such as GDPR (European Union) and CCPA (California) try to empower Internet users to control and own their information and content online. However, the golden rule of staying safe from online bullies and blackmailers is to never post anything that may reveal more than you intend, or come back to haunt you years later.
Even though it’s possible (and mandatory) for all online channels to delete your content should you wish so, you don’t have any control over the copies someone else may have created. With image recognition technology growing mature by the day it’s possible for anyone to:
- Upload a person’s image.
- Find out all images in the public web related to the person.
- Use the information to either carry out advanced social engineering attacks, or to hoard information for the purpose of blackmailing or misrepresenting anything in the future.
Parting Thoughts
Safety Rules In Electrical
Cyber safety is a continuous journey. Naturally, there won’t be an exhaustive list of best practices that will keep you safe. The five practices we’ve covered in this guide will help you remain safe and secure against the most commonly perpetrated cyber attacks.